Montagem e Reparação de computadores. Recuperação de dados. Suporte à sua empresa. Solicite já um orçamento! Contacte: errorsolutions.blogspot@gmail.com
Wednesday, November 23, 2016
Windows 7 - drag and drop / copy and past don't/doesn't work
1) Find an affected icon.(any in explorer or even in desktop)
2) Click and HOLD the icon with the Left mouse button.
3) Press Esc while holding the Left mouse button.
Monday, November 2, 2015
Drag and Drop Not Working in Windows 7
Then press the Escape key.
Drag and drop re-enabled.
Is the miracle of Microsoft! :)
Friday, May 30, 2014
Winsock Event viewer tracing
Using Event Viewer to Start Winsock Network Event Tracing
Using Event Viewer to Start Winsock Catalog Change Tracing
Audit service start and stop
Part of a service's security descriptor is the system ACL (SACL), which you can use to track access to that object.
The only way to view or change a service's current SACL is through security templates.
To reach the security templates, log on to the server and open the Microsoft Management Console (MMC) Security Templates snap-in.
To create a new template, right-click on the security templates path.
Select New Template, click System Services, then double-click the appropriate service (i.e., Telnet). Select the Define this policy setting in the template check box, then click Edit Security to open the Security for Telnet dialog box.
This dialog box contains the service's ACL, which you can use to fine-tune who has start and stop authority.
Click Advanced, then select the Auditing tab in the Access Control Settings for Telnet dialog box.
As you can see, no auditing is currently enabled on the Telnet service because auditing isn't enabled by default.
Click Add, then add an entry to track successful start and stop events that members of Everyone initiate.
Close all the dialog boxes, then save the template.
Import the template into the MMC Security Configuration and Analysis snap-in, then apply the template.
Now, you can check the Security log for event ID 560 (success audit: object open), where Object Type is SERVICE OBJECT, the Object Name is the short name of the service you're monitoring (in the case of the Telnet Service, TlntSvr), and the logged accesses include Start the service and Stop the service.
Source:
http://windowsitpro.com/systems-management/access-denied-auditing-users-who-might-be-starting-and-stopping-services
TCP retransmission
You can increase this value with registry key TcpMaxDataRetransmissions
Friday, February 22, 2013
The specified server cannot perform the requested operation
When trying to access from a machine to other is giving the error:
The specified server cannot perform the requested operation
Friday, November 9, 2012
MS-Dos - Internal commands/Batch file commands
Internal commands
- BREAK
- Controls the handling of program interruption with Ctrl+C or Ctrl+Break.
- CHCP
- Displays or changes the current system code page.
- CHDIR, CD
- Changes the current working directory or displays the current directory.
- CLS
- Clears the screen.
- COPY
- Copies one file to another (if the destination file already exists, MS-DOS asks whether to replace it). (See also XCOPY, an external command that could also copy directory trees).
- CTTY
- Defines the device to use for input and output.
- DATE
- Display and set the date of the system.
- DEL, ERASE
- Deletes a file. When used on a directory, deletes all files.
- DIR
- Lists the files in the specified directory.
- ECHO
- Toggles whether text is displayed (ECHO ON) or not (ECHO OFF). Also displays text on the screen (ECHO text).
- EXIT
- Exits from COMMAND.COM and returns to the program which launched it.
- LFNFOR
- Enables or disables the return of long filenames by the FOR command. (Windows 95/98/Me only).
- LOADHIGH, LH
- Loads a program into upper memory (HILOAD in DR DOS).
- LOCK
- Enables external programs to perform low-level disk access to a volume. (Windows 95/98/Me only).
- MKDIR, MD
- Creates a new directory.
- PATH
- Displays or changes the value of the PATH environment variable which controls the places where COMMAND.COM will search for executable files.
- PROMPT
- Displays or change the value of the PROMPT environment variable which controls the appearance of the prompt.
- REN, RENAME
- Renames a file or directory.
- RMDIR, RD
- Removes an empty directory.
- SET
- Sets the value of an environment variable ; Without arguments, shows all defined environment variables.
- TIME
- Display and set the time of the system.
- TRUENAME
- Display the fully expanded physical name of a file, resolving ASSIGN, JOIN and SUBST logical filesystem mappings.
- TYPE
- Display the content of a file on the console.
- UNLOCK
- Disables low-level disk access. (Windows 95/98/Me only)
- VER
- Displays the version of the operating system.
- VERIFY
- Enable or disable verification of writing for files.
- VOL
- Shows information about a volume.
[edit]Batch file commands
- :label
- Defines a target for GOTO.
- CALL
- Executes another batch file and returns to the old one and continues.
- FOR
- Iteration: repeats a command for each out of a specified set of files.
- GOTO
- Moves execution to a specified label. Labels are specified at the beginning of a line, with a colon (:likethis).
- IF
- Conditional statement, allows to branch the program execution.
- PAUSE
- Halts execution of the program and displays a message asking the user to press any key to continue.
- REM
- comment: any text following this command is ignored.
- SHIFT
- Replaces each of the command-line variables with the subsequent one (e.g. %0 with %1, %1 with %2 etc.).
Ms-Dos parameters/arguments - Batch files
| %~1 | - | expands %1 removing any surrounding quotes (") |
| %~f1 | - | expands %1 to a fully qualified path name |
| %~d1 | - | expands %1 to a drive letter only |
| %~p1 | - | expands %1 to a path only |
| %~n1 | - | expands %1 to a file name only |
| %~x1 | - | expands %1 to a file extension only |
| %~s1 | - | expanded path contains short names only |
| %~a1 | - | expands %1 to file attributes |
| %~t1 | - | expands %1 to date/time of file |
| %~z1 | - | expands %1 to size of file |
| %~$PATH:1 | - | searches the directories listed in the PATH environment variable and expands %1 to the fully qualified name of the first one found. If the environment variable name is not defined or the file is not found by the search, then this modifier expands to the empty string |
| %~dp1 | - | expands %1 to a drive letter and path only |
| %~nx1 | - | expands %1 to a file name and extension only |
| %~dp$PATH:1 | - | searches the directories listed in the PATH environment variable for %1 and expands to the drive letter and path of the first one found. |
| %~ftza1 | - | expands %1 to a DIR-like output line |
Friday, October 26, 2012
How to read windows dump file
http://msdn.microsoft.com/en-us/library/5a4x27ek.aspx
Install Windows Software Development Kit (SDK) for Windows 8
http://msdn.microsoft.com/en-US/windows/hardware/hh852363
Details:
http://support.microsoft.com/kb/315263/en-us?wa=wsignin1.0
symbol search path > http://msdl.microsoft.com/download/symbols
image source path > z:
my z: is the windows folder of a windows 2003 server installation because my dump is from windows 2003 server.
| Placeholder | Explanation |
|---|---|
| SymbolPath | Either the local path where the symbol files have been downloaded or the symbol server path, including a cache folder. Because a small memory dump file contains limited information, the actual binary files must be loaded together with the symbols for the dump file to be correctly read. |
| ImagePath | The path of these files. The files are contained in the I386 folder on the Windows XP CD-ROM. For example, the path may be C:\Windows\I386. |
| DumpFilePath | The path and file name for the dump file that you are examining. |
Using command-line
- Go to C:\Program Files (x86)\Windows Kits\8.0\Debuggers\x86 directory (in 32bits machine)
Example
- C:\Program Files (x86)\Windows Kits\8.0\Debuggers\x86> kd -y srv*c:\symbols*http://msdl.microsoft.com/download/symbols -i z:\ -z E:\my_dump_files\MEMORY.DMP
After the first info you can go deep writing:
- !analyze -v
To exit
- q
Using win app:
Start > all programs > windows kits > debugging tools for windows > windbg
File > symbol search path > http://msdl.microsoft.com/download/symbols
File > image source path > z:
click !analyze -v for deep analysis
Monday, October 15, 2012
RAID 10 Vs RAID 01 (RAID 1+0 Vs RAID 0+1)
RAID 10 is not the same as RAID 01.
RAID 10
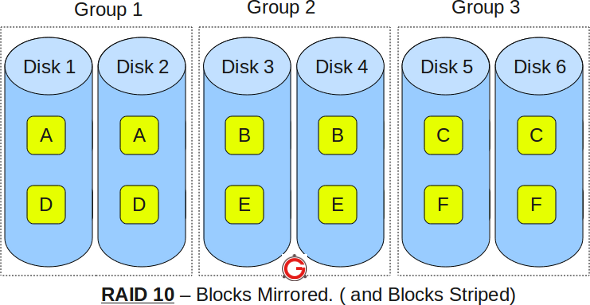
- RAID 10 is also called as RAID 1+0
- It is also called as “stripe of mirrors”
- It requires minimum of 4 disks
- To understand this better, group the disks in pair of two (for mirror). For example, if you have a total of 6 disks in RAID 10, there will be three groups–Group 1, Group 2, Group 3 as shown in the above diagram.
- Within the group, the data is mirrored. In the above example, Disk 1 and Disk 2 belongs to Group 1. The data on Disk 1 will be exactly same as the data on Disk 2. So, block A written on Disk 1 will be mirroed on Disk 2. Block B written on Disk 3 will be mirrored on Disk 4.
- Across the group, the data is striped. i.e Block A is written to Group 1, Block B is written to Group 2, Block C is written to Group 3.
- This is why it is called “stripe of mirrors”. i.e the disks within the group are mirrored. But, the groups themselves are striped.
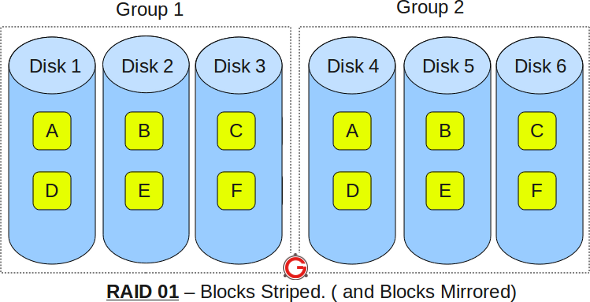
- RAID 01 is also called as RAID 0+1
- It is also called as “mirror of stripes”
- It requires minimum of 3 disks. But in most cases this will be implemented as minimum of 4 disks.
- To understand this better, create two groups. For example, if you have total of 6 disks, create two groups with 3 disks each as shown below. In the above example, Group 1 has 3 disks and Group 2 has 3 disks.
- Within the group, the data is striped. i.e In the Group 1 which contains three disks, the 1st block will be written to 1st disk, 2nd block to 2nd disk, and the 3rd block to 3rd disk. So, block A is written to Disk 1, block B to Disk 2, block C to Disk 3.
- Across the group, the data is mirrored. i.e The Group 1 and Group 2 will look exactly the same. i.e Disk 1 is mirrored to Disk 4, Disk 2 to Disk 5, Disk 3 to Disk 6.
- This is why it is called “mirror of stripes”. i.e the disks within the groups are striped. But, the groups are mirrored.
Main difference between RAID 10 vs RAID 01
- Performance on both RAID 10 and RAID 01 will be the same.
- The storage capacity on these will be the same.
- The main difference is the fault tolerance level. On most implememntations of RAID controllers, RAID 01 fault tolerance is less. On RAID 01, since we have only two groups of RAID 0, if two drives (one in each group) fails, the entire RAID 01 will fail. In the above RAID 01 diagram, if Disk 1 and Disk 4 fails, both the groups will be down. So, the whole RAID 01 will fail.
- RAID 10 fault tolerance is more. On RAID 10, since there are many groups (as the individual group is only two disks), even if three disks fails (one in each group), the RAID 10 is still functional. In the above RAID 10 example, even if Disk 1, Disk 3, Disk 5 fails, the RAID 10 will still be functional.
- So, given a choice between RAID 10 and RAID 01, always choose RAID 10.
- Gx is the name of the groups
- Dx is the name of the disks
For loosing your file, you need to loose G1 OR G2 OR G3. To loose G1, you need to loose D1 AND D2, to loose G2 you need to loose D3 AND D4 and to loose G3 you need to loose D5 AND D6.
=> probability of loosing your file : (f*f)+(f*f)+(f*f) = f²+f²+f² = 3f²
For loosing your file, you need to loose G1 AND G2. To loose G1 you need to loose D1 OR D2 OR D3, and to loose G2 you need to loose D4 OR D5 OR D6.
=> probability of loosing your file : (f+f+f)*(f+f+f)=3f*3f=9f²
- on RAID 10, if one disk fails, when the second failure appears, I have 1 possibility between 5 that this makes my entire system fail (the other disk in the group)
- on RAID 01, if one disk fails, when the second failure appears, I have 3 possibilities between 5 that this makes my entire system fail (any disk in the other group)
1,3 Up Up
1,4 Down Up
1,5 Down Up
1,6 Down Up
2,3 Up Up
2,4 Down Up
2,5 Down Up
2,6 Down Up
3,4 Down Down
3,5 Down Up
3,6 Down Up
4,5 Up Up
4,6 Up Up
5,6 Up Down
Some performance tests:
http://www.zdnet.com/blog/ou/comprehensive-raid-performance-report/484
Tuesday, January 10, 2012
Send to Location in Windows 7 (sendto)
Here it is....
Thursday, October 27, 2011
Environment variables / Variáveis de sistema
An environment variable is a dynamic value loaded into the memory that can be used by several processes operating simultaneously. On most operating systems, the location of some libraries or of the main system executables may be different depending on the installation.
It is therefore possible, from a given programme, to refer to a location based on the environment variables that define these data.
In Windows, the environment variables are placed between the "%" character. Thus to display the value of an environment variable, simply type following type of command:
echo %NAME_OF_THE_VARIABLE%Here is a non-exhaustive list of the main environment variables on Windows systems:
Environment variable Description
%APPDATA% Returns an access path to the default directory containing the user programmes (by default: C:\Program Files\.
%CMDCMDLINE% Returns the exact command used to access the command interpreter (cmd.exe).
%COMPUTERNAME% Returns the name attributed to the computer.
%DATE% Returns the day's date.
%ERRORLEVEL% Contains the error code of the latest command used.
%HOMEDRIVE% Contains the letter of the drive on which the current user's directory is located.
%HOMEDRIVE% Contains the letter of the drive on which the current user's directory is located.
%HOMEPATH% Contains the full access path to the current user's directory.
%NUMBER_OF_PROCESSOR% Contains the number of processors present on the system.
%OS% Contains a chain of characters describing the operating system installed. Note that Windows 2000 is identified as WINDOWS_NT.
%PATH% Specifies the access path to the system's main executables.
%PATHEXT% Describes the extensions that the system considers to be executable.
%PROCESSOR_ARCHITECTURE% Describes the architecture of the processor (x86 for Intel machines, IA64 for RISC architectures).
%RANDOM% Returns an integer between 0 and 32167 chosen at random by the system.
%SYSTEMDRIVE% Contains the letter of the drive on which the system is located (generally C:).
%SYSTEMROOT% Contains the access path to the system's root directory.
%TEMP% Contains the temporary directory access path for the applications.
%TMP% Contains the temporary directory access path for the applications.
%TIME% Returns the day's date.
%USERDOMAIN% Contains the domain to which the current account belongs.
%USERNAME% Contains the user name corresponding to the current account.
%USERPROFILE% Contains the location of the current account user profile.
%WINDIR% Contains the access path to the system's directory (generally C:\WINDOWS or C:\WINNT).
In Windows, the set command allows creation, modification and display of the environment variables. However, changes are made only in the session in progress.
To display a variable, the following command is used:
set VariableName To create a variable, the following command is used:
set VariableName=valueTo delete a variable, the following command is used:
set VariableName=It is possible to use any character as a value, including spaces. However, to be able to use special characters (<, >, , & or ^), simply place the (^) escape character in front of them or quotation marks around them, which will then be part of the value since all characters following the = sign are taken into account. For example, to define "black&white" as the value:
set colour=black^&white
or
set varname="new&name"
Thursday, July 28, 2011
Windows 7 ShortKeys and Shortcuts
Window Management Shortcuts
You can also interact with windows by dragging them with the mouse:
- Drag window to the top: Maximize
- Drag window left/right: Dock the window to fill half of the screen.
- Shake window back/forth: Minimize everything but the current window.
- Double-Click Top Window Border (edge): Maximize window vertically.
Taskbar Shortcuts
- Win+number (1-9): Starts the application pinned to the taskbar in that position, or switches to that program.
- Shift+Win+number (1-9): Starts a new instance of the application pinned to the taskbar in that position.
- Ctrl+Win+number (1-9): Cycles through open windows for the application pinned to the taskbar in that position.
- Alt+Win+number (1-9): Opens the Jump List for the application pinned to the taskbar.
- Win+T: Focus and scroll through items on the taskbar.
- Win+B: Focuses the System Tray icons
In addition, you can interact with the taskbar using your mouse and a modifier key:
- Shift+Click on a taskbar button: Open a program or quickly open another instance of a program.
- Ctrl+Shift+Click on a taskbar button: Open a program as an administrator.
- Shift+Right-click on a taskbar button: Show the window menu for the program (like XP does).
- Shift+Right-click on a grouped taskbar button: Show the window menu for the group.
- Ctrl+Click on a grouped taskbar button: Cycle through the windows of the group.
More Useful Hotkeys You Should Know
- Ctrl+Shift+N: Creates a new folder in Windows Explorer.
- Alt+Up: Goes up a folder level in Windows Explorer.
- Alt+P: Toggles the preview pane in Windows Explorer.
- Shift+Right-Click on a file: Adds Copy as Path, which copies the path of a file to the clipboard.
- Shift+Right-Click on a file: Adds extra hidden items to the Send To menu.
- Shift+Right-Click on a folder: Adds Command Prompt Here, which lets you easily open a command prompt in that folder.
- Win+P: Adjust presentation settings for your display.
- Win+(+/-): Zoom in/out.
- Win+G: Cycle between the Windows Gadgets on your screen.
Others:
Win+UP Arrow :- Maximize the current window
Win+Down Arrow :- If the current window is maximized, restore it; if the current window is restored, minimize it
Win+Left Arrow :- Dock the current window to the left half of the screen
Win+Right Arrrow :- Dock the current window to the right half of the screen
Win+Home :- Minimize all but the current window
Win+P :- Open the projection menu (generally used for laptops connected to projectors)
Alt+F4 :- Close the active window
Alt+Tab :- Switch to previous active window
Alt+Esc :- Cycle through all open windows
Win+Tab :- Flip 3D
Ctrl+Win+Tab :- Persistent Flip 3D
Win+T :- Cycle through applications on taskbar (showing its live preview)
Win+M :- Minimize all open windows
Win+Shift+M :- Undo all window minimization
Win+D :- Toggle showing the desktop
Win+Up Arrow :- Maximize the current window
Win+Down Arrow :- If the current window is maximized, restore it; if the current window is restored, minimize it
Win+Left Arrow :- Dock the current window to the left half of the screen
Win+Right Arrow :- Dock the current window to the right half of the screen
Win+Home :- Minimize all but the current window
Wednesday, November 4, 2009
Using Group Policy to Deploy Applications
The technique that I’m about to show you will allow you to deploy applications through the Active Directory. One of the major limitations behind this type of application deployment is that you can only use this technique to deploy certain types of applications. Specifically, you can install Windows Installer packages (.MSI files), Transform Files (.MST files), and patch files (.MSP files).
Creating MSI Files
Windows does not natively contain the necessary tools for you to create your own MSI files. Instead, you will have to rely on a third party MSI creation tool. There are several good tools available for free. Two of the more popular choices are MAKEMSI (http://dennisbareis.com/makemsi.htm) and WinInstall LE 2003 (http://www.ondemandsoftware.com/freele.asp).
Being that I’ve never been a big fan of script writing, I prefer to use the WinInstall LE tool to create MSI files. It doesn’t require any scripting, but it is a little time consuming to use. WinInstall LE requires you to have a machine with a clean Windows installation and network connectivity. The software then takes a snapshot of this machine and saves the configuration image. You would then install the application that you want to create the MSI file for and take another snap shot. WinInstall would then compare the snapshots and use the differences between the two images to create an MSI file and the corresponding installation package.
This method is a little time consuming, but is far less tedious than writing scripts. Another advantage to using this method is that it is possible to install multiple applications on to the clean machine prior to taking the second snap shot. This means that you can create a single MSI file and installation package that deploys multiple applications.
Publishing and Assigning Applications
Now that you know how to create an MSI file, there is one last concept that I need to talk about before I show you how to deploy an application thorough the Active Directory.
As you may already know, in an Active Directory environment, group policies are the main component of network security. Group policy objects can be applied either to users or to computers. Deploying applications through the Active Directory is also done through the use of group policies, and therefore applications are deployed either on a per user basis or on a per computer basis.
There are two different ways that you can deploy an application through the Active Directory. You can either publish the application or you can assign the application. You can only publish applications to users, but you can assign applications to either users or to computers. The application is deployed in a different manner depending on which of these methods you use.
Publishing an application doesn’t actually install the application, but rather makes it available to users. For example, suppose that you were to publish Microsoft Office. Publishing is a group policy setting, so it would not take effect until the next time that the user logs in. When the user does log in though, they will not initially notice anything different. However, if the user were to open the Control Panel and click on the Add / Remove Programs option, they will find that Microsoft Office is now on the list. A user can then choose to install Microsoft office on their machine.
One thing to keep in mind is that regardless of which deployment method you use, Windows does not perform any sort of software metering. Therefore, it will be up to you to make sure that you have enough licenses for the software that you are installing.
Assigning an application to a user works differently than publishing an application. Again, assigning an application is a group policy action, so the assignment won’t take effect until the next time that the user logs in. When the user does log in, they will see that the new application has been added to the Start menu and / or to the desktop.
Although a menu option or an icon for the application exists, the software hasn’t actually been installed though. To avoid overwhelming the server containing the installation package, the software is not actually installed until the user attempts to use it for the first time.
This is also where the self healing feature comes in. When ever a user attempts to use the application, Windows always does a quick check to make sure that the application hasn’t been damaged. If files or registry settings are missing, they are automatically replaced.
Assigning an application to a computer works similarly to assigning an application to a user. The main difference is that the assignment is linked to the computer rather than to the user, so it takes effect the next time that the computer is rebooted. Assigning an application to a computer also differs from user assignments in that the deployment process actually installs the application rather than just the application’s icon.
Deploying Applications
Setting up the actual deployment is simple. The biggest thing that you must remember is that the MSI file and the corresponding package must exist within a network share, and everyone must have read permissions for that share.
To perform the deployment, open the Group Policy Editor. To publish or assign an application to a user, navigate through the group policy console to User Configuration Software Settings Software Installation. Now, right click on the Software Installation container and select the New Package commands from the shortcut menu. Select the appropriate MSI file and click Open. You are now asked whether you want to publish or assign the application. Make your selection and click OK.
The process for assigning an application to a computer is almost identical. The only real difference is that you would use the Software Settings Software Installation container beneath the Computer Configuration container rather than beneath the User Configuration container.
See also (for unatended installation):
http://unattended.sourceforge.net/installers.php
Tuesday, November 3, 2009
Performance Counters - Open a saved log (blg file)
2. Click the icon on the System Monitor that has the database symbol (a cylinder) and browse to the location where you saved the log file (BLG).
3. Click Add (a plus) to add the objects you monitored.
Performance Counters - Disks Fast Enough?
Performance Counter - Got Enough RAM?
You should do two things with the Memory\Available Bytes counter: create a performance log for this counter and monitor it regularly to see if any downward trend develops, and set an alert to trigger if it drops below 2% of the installed RAM. If a downward trend does develop, you can monitor Process(instance)\Working Set for each process instance to determine which process is consuming larger and larger amounts of RAM. Process(instance)\Working Set measures the size of the working set for each process, which indicates the number of allocated pages the process can address without generating a page fault. A related counter is Memory\Cache Bytes, which measures the working set for the system i.e. the number of allocated pages kernel threads can address without generating a page fault.
Finally, another corroborating indicator of insufficient RAM is Memory\Transition Faults/sec, which measures how often recently trimmed page on the standby list are re-referenced. If this counter slowly starts to rise over time then it could also indicating you're reaching a point where you no longer have enough RAM for your server to function well